Our latest guest blog is kindly written by Niall Quinn from HTG.
Picture this: You’ve invested in IT (either directly or via an IT managed service provider), with firewalls, employee training, and security software. But would you bet your business on your suppliers’ security practices? According to the UK Government’s 2025 Cyber Security and Resilience Policy Statement, while most businesses check vendor security, only 31% actually include cybersecurity provisions in their contracts.
Cyber Security and Resilience Bill
Do You Know If Your Supply Chain Is Secure?
Ask yourself these questions:
- Does your accountant who handles your financial data have cybersecurity terms in their contract?
- What about your cleaning company with after-hours access to your offices?
- Is your HR outsourcing partner who manages employee records contractually required to notify you of a breach?
- Does your marketing agency with access to your customer database have security obligations?
If you’re like most business owners, the answer is probably no
Your Biggest Cyber Risk: Suppliers Without Basic Protection
For what it is worth, any supplier and/or provider who has access to your systems or data and doesn’t have Cyber Essentials as a MINIMUM, is the biggest cybersecurity risk to you, your business AND your customers.
Think about it: You wouldn’t hire an uninsured contractor to work on your premises, so why give network access to suppliers without basic security certifications?
When Your Breach Becomes Your Customers’ Breach
Remember, if your accountant’s system is breached, and they can access your customer systems and/or data, then your customers are now at risk too. Your business doesn’t exist in isolation—it’s part of an interconnected web of trust.
Understanding the Domino Effect: How Attackers Move Through Your System
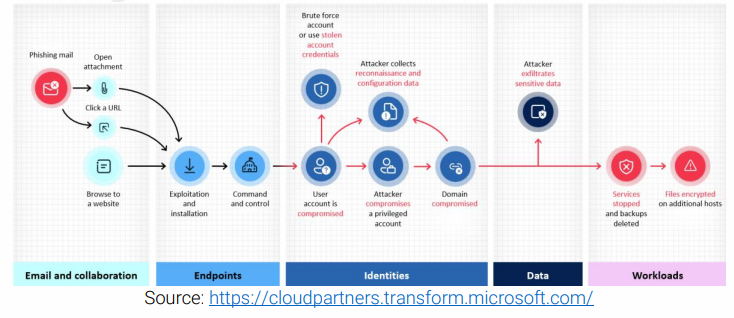
The Hidden Danger: How Hackers Use Your Suppliers to Get to You
Think of your business network like a neighbourhood. Your suppliers have keys to specific doors in your house because they need access to do their jobs:
- Your accountant has a key to your financial records room
- Your HR provider has a key to your personnel files
- Your IT provider has master keys to almost everything
When hackers break into your supplier’s systems, it’s like they’ve stolen these keys. Now they
can:
- Walk right through your front door using legitimate credentials/hacked accounts (no alarms triggered)
- Move from room to room inside your business, looking for valuable information
- Make copies of more keys they find inside, gaining access to restricted areas
- Eventually reach your vault where your most sensitive customer data is stored
- Exit with the valuables, often without you even knowing they were there
Your security systems might not flag this activity because it looks like your trusted supplier accessing your systems—just as they do every day.
Remember, your business or systems might be used as a gateway for attackers targeting your customers or suppliers. You may not be the target.
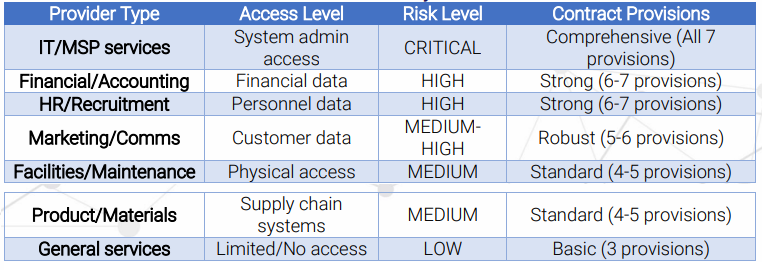
Quick Risk Assessment: Who Needs Security Provisions?
Seven Essential Contract Provisions Every Business Owner Needs
- Breach Notification Requirements
What it means for you: If your payroll provider is breached, how quickly will they tell you?
Without contractual terms, they might not tell you at all.
Make it happen: “Supplier must notify us within 24 hours of discovering any security incident that could affect our data or operations.” - Incident Response Responsibilities
What it means for you: When your IT provider discovers a breach, who pays for investigation and recovery? Without clear terms, you’ll be footing the bill.
Make it happen: “Supplier will provide immediate technical assistance during security incidents at no additional cost for the first 48 hours.” - Compliance with Security Standards
What it means for you: That small accounting firm handling your finances—are they following any security standards at all?
Make it happen: “Supplier must maintain at minimum Cyber Essentials certification and provide evidence annually.” - Right to Audit and Test
What it means for you: Can you verify your marketing agency’s security claims, or must you take their word for it?
Make it happen: “We reserve the right to conduct security assessments with 5 days’ notice.” - Data Protection and Privacy Obligations
What it means for you: Does your recruitment agency know how to properly handle, store, and eventually delete candidate data?
Make it happen: “All data must be encrypted both in transit and at rest, with documented deletion procedures at contract end.” - Security Event Reporting
What it means for you: If your logistics partner notices suspicious activity but stops it before a breach, will they tell you about the near-miss?
Make it happen: “Supplier must report all security events, including unsuccessful attempts, that could have affected our data.” - Liability and Indemnification
What it means for you: If your supplier’s poor security practices lead to your business being fined £100,000, who pays?
Make it happen: “Supplier will indemnify us against losses resulting from their failure to maintain appropriate security measures.”
Four Things You Can Do TODAY to Protect Your Business
- Turn on Multi-Factor Authentication (MFA) – This should be non-negotiable for all accounts that access your business systems. MFA stops 99% of account compromise attacks.
- Update All Devices – Ensure your computers, phones, and other devices have the latest security patches and updates. Many breaches exploit known vulnerabilities that updates would have fixed.
- Send the Email Template to Your Suppliers – Use the template below to contact your key suppliers TODAY and verify their cybersecurity protections for your business.
- Review the NCSC Website – The National Cyber Security Centre has excellent guides and resources for businesses of all sizes. Visit ncsc.gov.uk for practical, actionable advice.
Supplier Email Template (free to use to send to your supplier(s))
Subject: Urgent: Security Requirements for Continued Partnership
Dear [Supplier Name],
Recent security assessments have highlighted a critical gap in our supplier contracts. As cybersecurity incidents increase across the UK, we’re updating all supplier contracts to include essential security provisions.
As a valued partner with access to our [systems/data/facilities], we need to formalise security expectations with:
- Prompt security incident notification (24 hours)
- Clear incident response responsibilities
- Verified security standards compliance (minimum Cyber Essentials)
- Reasonable audit rights
- Data protection requirements
- Security event reporting
- Fair liability allocation
Please share your current security certifications (Cyber Essentials, Cyber Essentials Plus, or ISO 27001 if applicable) by X Date
These updates are not just regulatory compliance – they’re essential protection for both our businesses. The new UK Cyber Security and Resilience Bill makes these provisions increasingly important.
I appreciate your partnership in strengthening our security posture.
Regards,
[Your Name]
Take action today:
- Identify which suppliers have access to your systems or data
- Prioritise them using the risk matrix above
- Update contracts starting with your highest-risk providers
- Use the email template to start the conversation. Remember: Your security is only as strong as your weakest supplier link. And without contractual protections, that link is completely outside your control.
Thanks to Niall Quinn from HTG for this guest blog, HTG deliver fully managed IT and security services, built on Microsoft’s best practices, to keep your business secure and productive—without the complexity.
